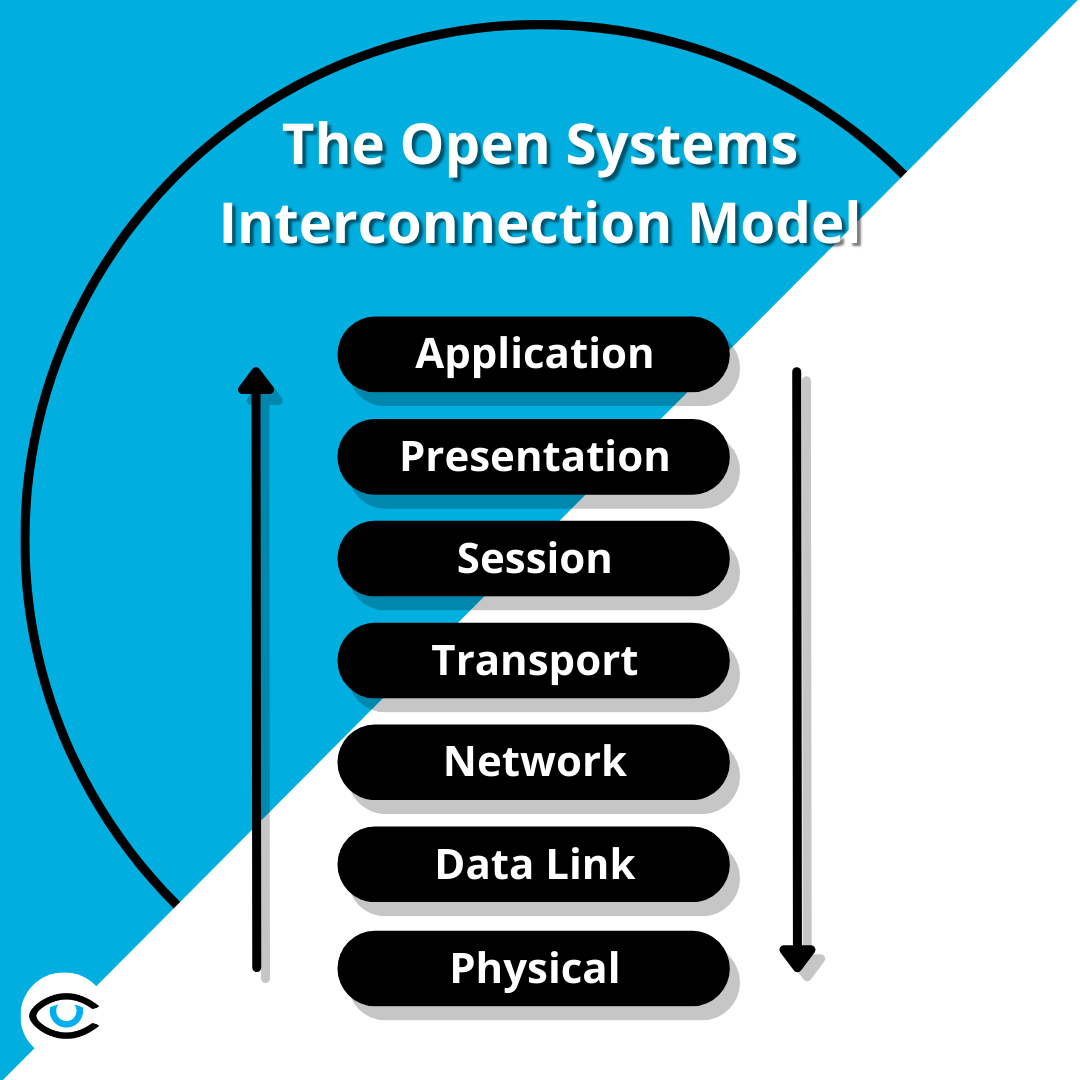
The Open Systems Interconnection model, or OSI for short, is a conceptual framework which describes the seven layers that computer systems use to communicate over a network. The OSI model characterizes computing functions into a universal set of rules and requirements in order to support interoperability between different products and software. In the OSI reference model, the communications between a computing system are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application (Source).
A Brief History of the OSI Model and How It Works
Published in 1983 and adopted in 1984 by the International Organization for Standardization, the OSI model is still heavily utilized today as a means to describe network architecture and relationships between various constituents within a system. Each layer in the OSI Model is comprised of multiple protocols which form a protocol stack.
A protocol stack is a group of protocols arranged on top of each other as part of a communication process. Each layer of the OSI model has different protocols associated with it. Each layer in the protocol stack receives services from the layer below it and provides services to the layer above it. For two different computers to communicate, the same protocol stack must be running on each computer. (Source)
When a message is sent from one machine to another, it travels down the layers of one machine and then up the layers on the receiving computer. As the message travels down the first stack, each layer it passes through adds a header. This header contains control information that is read and processed by the corresponding layer on the receiving computer. As the message travels up the stack of the receiving machine, each layer strips off the header added by the corresponding layer of the sending computer. (Source)
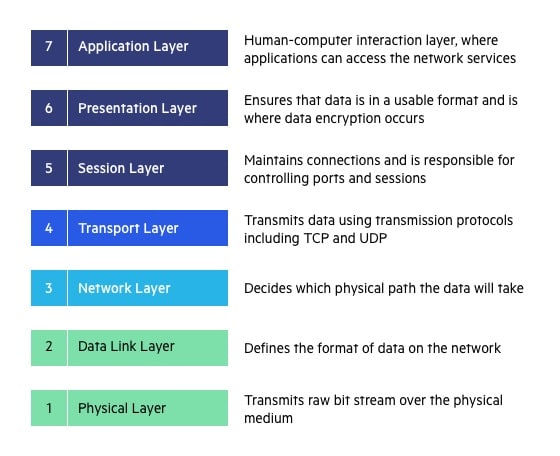
Physical Layer
The lowest layer of the OSI Model is concerned with electrically or optically transmitting raw unstructured data bits across the network from the physical layer of the sending device to the physical layer of the receiving device. It can include specifications such as voltages, pin layout, cabling, and radio frequencies. At the physical layer, one might find “physical” resources such as network hubs, cabling, repeaters, network adapters or modems.
Data Link Layer
At the data link layer, directly connected nodes are used to perform node-to-node data transfer where data is packaged into frames. The data link layer also corrects errors that may have occurred at the physical layer.
The data link layer encompasses two sub-layers of its own. The first, media access control (MAC), provides flow control and multiplexing for device transmissions over a network. The second, the logical link control (LLC), provides flow and error control over the physical medium as well as identifies line protocols.
Network Layer
The network layer is responsible for receiving frames from the data link layer, and delivering them to their intended destinations among based on the addresses contained inside the frame. The network layer finds the destination by using logical addresses, such as IP (internet protocol). At this layer, routers are a crucial component used to quite literally route information where it needs to go between networks.
Transport Layer
The transport layer manages the delivery and error checking of data packets. It regulates the size, sequencing, and ultimately the transfer of data between systems and hosts. One of the most common examples of the transport layer is TCP or the Transmission Control Protocol.
Session Layer
The session layer controls the conversations between different computers. A session or connection between machines is set up, managed, and termined at layer 5. Session layer services also include authentication and reconnections.
Presentation Layer
The presentation layer formats or translates data for the application layer based on the syntax or semantics that the application accepts. Because of this, it at times also called the syntax layer. This layer can also handle the encryption and decryption required by the application layer.
Application Layer
At this layer, both the end user and the application layer interact directly with the software application. This layer sees network services provided to end-user applications such as a web browser or Office 365. The application layer identifies communication partners, resource availability, and synchronizes communication. (Source)
Have More Questions?
Feel free to reach out to us if you have any questions or concerns! Our cybersecurity professionals will be more than happy to help you with anything you need. Book an appointment with us today!